openswan IPSec
简介
本文介绍IPSecVPN的搭建过程,并通过公网将分属于美团云上海与北京两个机房内的vpc子网打通。
由于美团云经典网络在网络控制器上对ip_filter 做了限制,打通前需要确保两边网络都处于VPC下,且子网网段无交集。
当前部署环境为CentOS 6.5。
一、网络模型
计划实现的效果是,从左侧vpc网络上的left-client主机,可以ping通右侧vpc中right-client主机内网IP
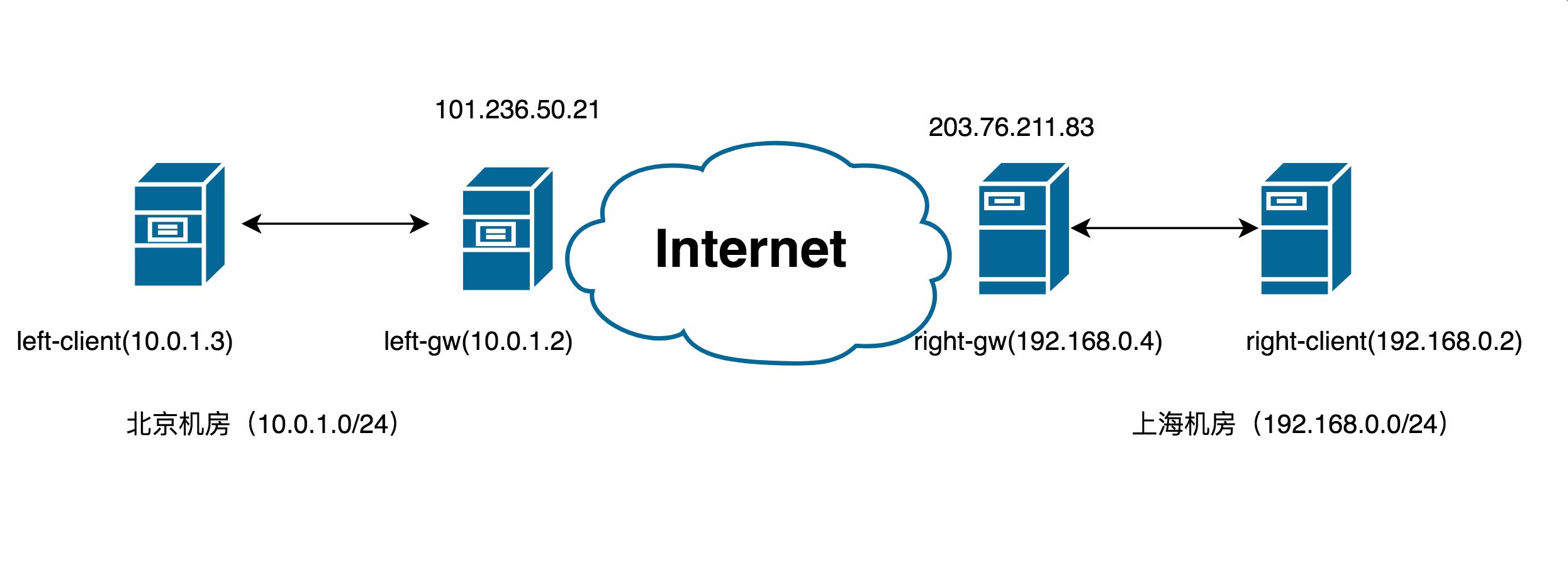
二、环境配置
此处环境配置,主要是针对两台用做gw的主机:left-gw和right-gw
1 内核参数
# vim /etc/sysctl.conf
net.ipv4.ip_forward = 1
net.ipv4.conf.default.rp_filter = 0
net.ipv4.conf.eth0.rp_filter = 0
net.ipv4.conf.eth1.rp_filter = 0
关闭icmp重定向
# sysctl -a | egrep "ipv4.*(accept|send)_redirects" | awk -F "=" '{print$1"= 0"}' >> /etc/sysctl.conf
# sysctl -p
2 OpenSwan配置
通过yum安装OpenSwan (ipsec)
sudo yum -y install openswan
安装完毕后,可以看到实际安装的版本为Libreswan3.15 , 是因为最原始的OpenSwan已不再更新。
# ipsec --version
Linux Libreswan 3.15 (netkey) on 2.6.32-696.1.1.el6.x86_64
执行下ipsec verify,确认配置正常:
# ipsec verify
Verifying installed system and configuration files
Version check and ipsec on-path [OK]
Libreswan 3.15 (netkey) on 2.6.32-431.1.2.0.1.el6.x86_64
Checking for IPsec support in kernel [OK]
NETKEY: Testing XFRM related proc values
ICMP default/send_redirects [OK]
ICMP default/accept_redirects [OK]
XFRM larval drop [OK]
Pluto ipsec.conf syntax [OK]
Hardware random device [N/A]
Two or more interfaces found, checking IP forwarding [OK]
Checking rp_filter [OK]
Checking that pluto is running [OK]
Pluto listening for IKE on udp 500 [OK]
Pluto listening for IKE/NAT-T on udp 4500 [OK]
Pluto ipsec.secret syntax [OK]
Checking 'ip' command [OK]
Checking 'iptables' command [OK]
Checking 'prelink' command does not interfere with FIPSChecking for obsolete ipsec.conf options [OK]
Opportunistic Encryption [DISABLED]
vim /etc/ipsec.conf 编辑配置文件
version 2
# basic configuration
config setup
# which IPsec stack to use, "netkey" (the default), "klips" or "mast".
# For MacOSX use "bsd"
protostack=netkey //使用2.6内核内建模块netkey,2.6以下是KLIPS模块
nat_traversal=yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:25.0.0.0/8,%v4:100.64.0.0/10,%v6:fd00::/8,%v6:fe80::/10
dumpdir=/var/run/pluto/
logfile=/var/log/pluto.log //log location
conn net-to-net
authby=secret //使用预共享密钥方式进行认证
type=tunnel
left=101.236.50.21
leftsubnet=10.0.1.0/24
leftid=@test1 //一端的标识符,可以任意填写,如果多个连接需要区分
leftnexthop=%defaultroute
right=203.76.211.83
rightsubnet=192.168.0.0/24
rightid=@test2
rightnexthop=%defaultroute
ike=aes256-sha2_256;modp2048
phase2alg=aes256-sha2_256;modp2048
auto=add //add代表只是添加,但并不会连接,如果为start则代表着启动自动连接
两台主机是完全相同的配置,可以直接将ipsec.conf的配置文件scp 到另一台gw server上
我们使用基于pre-shared keys认证方式(PSK), 在101.236.50.21上:
vim /etc/ipsec.secrets
101.236.50.21 %any 0.0.0.0 : PSK "123"
这个文件的格式为:“Local Ip address” “remote ip address” : PSK “your key”
若本身不存在/etc/ipsec.secrets ,可以执行下述命令先生成此文件:
ipsec newhostkey --output /etc/ipsec.secrets
同理在右侧right-gw机器上也做相应配置。
重启两个vpn服务:
service ipsec restart
在其中一台主机上启动connect:
# ipsec auto --up net-to-net
002 "net-to-net" #1: initiating Main Mode
104 "net-to-net" #1: STATE_MAIN_I1: initiate
003 "net-to-net" #1: received Vendor ID payload [Dead Peer Detection]
003 "net-to-net" #1: received Vendor ID payload [FRAGMENTATION]
003 "net-to-net" #1: received Vendor ID payload [RFC 3947]
002 "net-to-net" #1: enabling possible NAT-traversal with method RFC 3947 (NAT-Traversal)
002 "net-to-net" #1: transition from state STATE_MAIN_I1 to state STATE_MAIN_I2
106 "net-to-net" #1: STATE_MAIN_I2: sent MI2, expecting MR2
003 "net-to-net" #1: NAT-Traversal: Result using RFC 3947 (NAT-Traversal) sender port 500: no NAT detected
002 "net-to-net" #1: transition from state STATE_MAIN_I2 to state STATE_MAIN_I3
108 "net-to-net" #1: STATE_MAIN_I3: sent MI3, expecting MR3
003 "net-to-net" #1: received Vendor ID payload [CAN-IKEv2]
002 "net-to-net" #1: Main mode peer ID is ID_FQDN: '@test2'
002 "net-to-net" #1: transition from state STATE_MAIN_I3 to state STATE_MAIN_I4
004 "net-to-net" #1: STATE_MAIN_I4: ISAKMP SA established {auth=PRESHARED_KEY cipher=aes_256 integ=sha group=MODP2048}
002 "net-to-net" #2: initiating Quick Mode PSK+ENCRYPT+TUNNEL+PFS+UP+IKEV1_ALLOW+IKEV2_ALLOW+SAREF_TRACK+IKE_FRAG_ALLOW {using isakmp#1 msgid:f72303da proposal=defaults pfsgroup=OAKLEY_GROUP_MODP2048}
117 "net-to-net" #2: STATE_QUICK_I1: initiate
002 "net-to-net" #2: transition from state STATE_QUICK_I1 to state STATE_QUICK_I2
004 "net-to-net" #2: STATE_QUICK_I2: sent QI2, IPsec SA established tunnel mode {ESP=>0x5e6e7359 <0x2442c77b xfrm=AES_128-HMAC_SHA1 NATOA=none NATD=none DPD=passive}
可以看到 “IPsec SA established tunnel mode” 连接已建立
3 添加路由
由于vpn网关的功能还未上线公有云,需要在vm内部添加路由:
在10.0.1.3 (left-client)上,执行:
# route add -net 192.168.0.0/24 gw 10.0.1.2 dev eth0 ## 将访问右侧子网的路由指向到左侧网关主机(left-gw)
在101.236.50.21 (left-gw)上,执行:
# route add -net 192.168.0.0/24 gw 101.236.50.21 dev eth1 ## 将访问右侧子网的路由指向到本机公网IP,使之通过ipsec隧道出去
在203.76.211.83 (right-gw)上执行 :
# route add -net 10.0.1.0/24 gw 203.76.211.83 dev eth1 ## 将访问左侧子网默认路由指向本机公网IP
在192.168.0.2(right-client)上执行:
# route add -net 10.0.1.0/24 gw 192.168.0.4 dev eth0 ## 将访问左侧子网的路由指向right-gw机器内网IP。
四、验证
从left-client主机 去ping right-client机器的内网IP,确认网络已打通。
另外需要注意,两台gw的vm是无法直接ping通对方内网的。
# ifconfig eth0
eth0 Link encap:Ethernet HWaddr 00:22:40:CA:A9:27
inet addr:10.0.1.3 Bcast:10.0.1.255 Mask:255.255.255.0
inet6 addr: fe80::222:40ff:feca:a927/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:60102 errors:0 dropped:0 overruns:0 frame:0
TX packets:17631 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:4539749 (4.3 MiB) TX bytes:1410635 (1.3 MiB)
# ping 192.168.0.2
PING 192.168.0.2 (192.168.0.2) 56(84) bytes of data.
64 bytes from 192.168.0.2: icmp_seq=1 ttl=62 time=26.5 ms
64 bytes from 192.168.0.2: icmp_seq=2 ttl=62 time=26.0 ms
64 bytes from 192.168.0.2: icmp_seq=3 ttl=62 time=26.0 ms
64 bytes from 192.168.0.2: icmp_seq=4 ttl=62 time=26.0 ms
^C:q!
--- 192.168.0.2 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3371ms
rtt min/avg/max/mdev = 26.006/26.164/26.534/0.214 ms
总结
本文是基于预共享密钥(PSK)的认证方式;其他还有基于RSA Signature认证方式(RSA数字签名),以及基于数字证书认证方式(x.509证书)等。
相关文章
- IPv6 tutorial 3 New features: IPsec and LAN features
- HCIE-Security Day42:IPsec高可用技术
- HCIE-Security Day35:IPSec-NAT-T
- HCIE-Security Day33:IPSec:深入学习ipsec ikev2、IKEV1和IKEV2比较
- HCIE-Security Day32:IPSec:深入学习ipsec ikev1、主模式、野蛮模式、快速模式、dh算法、预共享密钥
- HCIE-Security Day31:IPSec:实验(六)配置PPPoE拨号分支与总部建立IPSec隧道示例
- HCIE-Security Day30:IPSec:实验(五)配置基于路由的IPSec PN(采用预共享密钥认证)
- HCIE-Security Day29:IPSec:实验(四)总部与分支机构之间建立IPSec PN(采用策略模板方式,总部采用固定IP)
- HCIE-Security Day28:IPSec:实验(三)总部采用ISAKMP方式安全策略组与分支机构之间建立IPSec PN
- HCIE-Security Day27:IPSec:实验(二)两个网关之间通过手工方式创建IPSec PN隧道
- HCIE-Security Day26:IPSec:实验(一)两个网关之间通过IKE方式协商IPSec PN隧道(采用预共享密钥认证)
- Windows IPsec IP安全策略
- 计算机网络4小时速成:网络安全,被动攻击,主动攻击,对称加密,公钥秘钥,数字签名,鉴别,网络层安全协议IPsec,传输层安全协议SSL,防火墙,入侵检测系统
- 生产环境l2tp/ipsec配置
- IPSec配置
- 在CentOS上使用strongSwan搭建IPsec V P N服务
- 脚本搭建l2tp/IPSec
- 华为防火墙l2tp/ipsec搭建xxx配置
- l2tp/ipsec搭建xxx
- WIN10系统使用自带软件进行L2TP over IPSec拨号时的配置示例
- 华三IPsec
- 华为GRE over IPsec的配置思路原理以及安全策略的设置
- 华为IPsec隧道模式能否做到路由协议的动态传播
- H3C IPsec穿越nat实验
- 有关windows Gateway Ipsec 和NAT 兼容性问题

