某影视APP算法逆向分析
2023-03-14 22:47:22 时间
一、抓取数据包
1、请求头有%加十六进制,说以是url编码,先解密一下
GET http://m.mapps.m1905.cn/User/sendVer?request=jYgPer7AuEqdM+DYqs/AbNb35UrMvjLwt4+f0p3RHXc= HTTP/1.12、需要找的数值是requests的组成、pid(常量值)、key、did(设备编号)
GET http://m.mapps.m1905.cn/User/sendVer?request=jYgPer7AuEqdM%2BDYqs%2FAbNb35UrMvjLwt4%2Bf0p3RHXc%3D HTTP/1.1 sid: pid: 236 key: 69b39cb24632252f7bb891bdb1f0de85 did: 010067028741939 uid: ver: 100/95/2016020901 User-Agent: Dalvik/2.1.0 (Linux; U; Android 7.1.2; HD1900 Build/N2G47O) Host: m.mapps.m1905.cn Connection: Keep-Alive Accept-Encoding: gzip
二、搜索链接里关键字"User/sendVer"
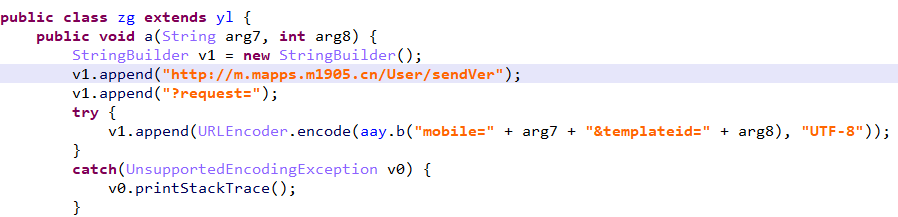
1、查看aay.b()函数,DESede算法
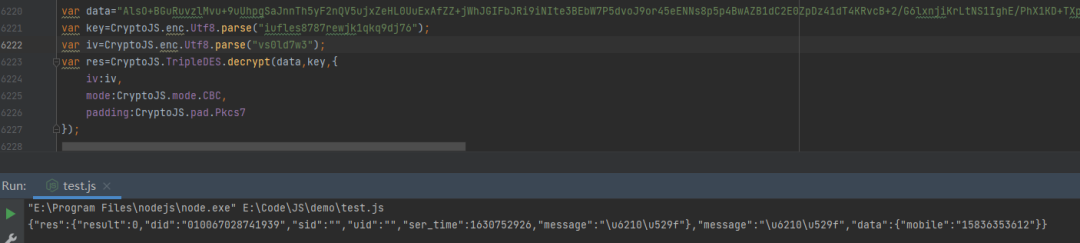
key:iufles8787rewjk1qkq9dj76,iv:vs0ld7w3
2、由于DESede是对称加密算法,密文是:jYgPer7AuEqdM+DYqs/AbNb35UrMvjLwt4+f0p3RHXc=,可以反推一下得到加密内容为:mobile=15836353612&templateid=1
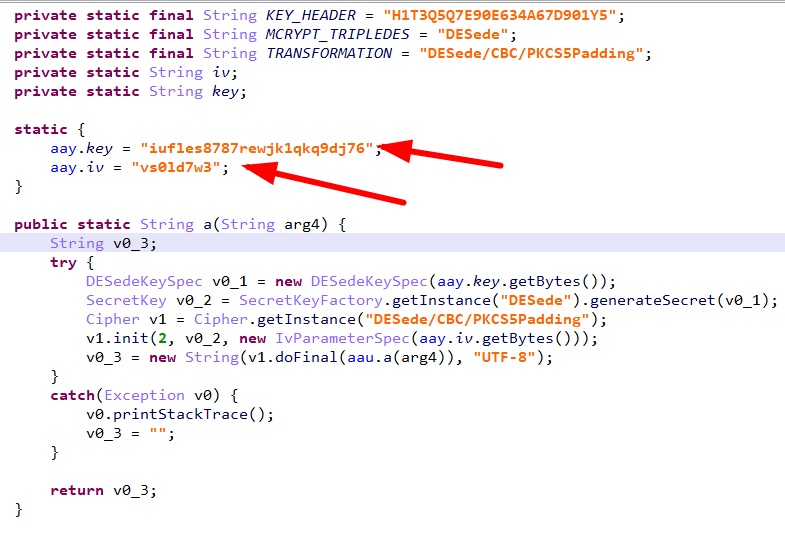
三、搜索关键字key

1、查看v0.i()函数
public String i() { return abh.a(abb.c() + "m1905_2014"); }
2、查看abb.c()函数,获取设备id
public static String c() { String v0_2; try { TelephonyManager v0_1 = (TelephonyManager)BaseApplication.a().getSystemService("phone"); v0_2 = v0_1 == null ? "" : v0_1.getDeviceId(); } catch(Exception v0) { v0_2 = ""; } return v0_2; }
3、查看abh.a()函数,获取md5值
public class abh { public static final String a(String arg9) { int v0 = 0; if(!TextUtils.isEmpty(arg9)) { char[] v2 = new char[]{'0', '1', '2', '3', '4', '5', '6', '7', '8', '9', 'a', 'b', 'c', 'd', 'e', 'f'}; try { byte[] v1 = arg9.getBytes(); MessageDigest v3 = MessageDigest.getInstance("MD5"); v3.update(v1); byte[] v3_1 = v3.digest(); char[] v5 = new char[(((int)v1)) * 2]; int v1_1 = 0; while(v0 < v3_1.length) { int v6 = v3_1[v0]; int v7 = v7 + 1; char v8 = v2[v8 >>> 4 & 15]; v5[v1_1] = v8; ++v1_1; v5[v7] = v2[v6 & 15]; ++v0; } arg9 = new String(v5); } catch(Exception v0_1) { arg9 = null; } } return arg9; } }
4、最终就是设备id+m1905_2014,然后再算md5
四、响应值解密
禁止非法,后果自负
相关文章
- Chrome DevTools 远程调试安卓网页的原理
- Uni-app + Vue3 页面如何跳转及传参?
- 微软证实系统还原点会损坏 Windows 11 22H2 版本应用程序
- 巧用 Transition 实现短视频 APP 点赞动画
- 初学者试试,HarmonyOS应用开发者基础认证
- 媒体实测微软 Windows 开发工具包 2023:存在不兼容 HDR 显示器、某些应用无法运行等问题
- 快速了解Navigator API SetAppBadge
- 微软 Windows 11 Dev 预览版 Build 25276 发布,应用兼容问题对话框 UI 改进
- 基于Next.js、Prisma、Postgres和Fastfy构建全栈APP
- 开始菜单搜索框变圆角,微软 Windows 11 Beta 预览版 22621.1095 和 22623.1095 发布
- 2022-2023 十大应用开发趋势
- 观远数据发布业内首部《移动BI白皮书》,深入业务数字化场景重新定义移动BI
- Windows 10 学院:不借助第三方工具如何卸载 Windows 10 预装应用
- 正处高质量发展期,我国大数据产业突破1.3万亿元
- 大数据技术在金融行业的应用与安全风险管理
- 基于鸿联标准系统开发板的毛泽东诗文应用
- 为Wifi-lot小车做一个遥控器应用
- OpenHarmony应用集成AGC认证服务实现登录
- 如何在React中应用SOLID原则?
- 为什么大热的数据可视化行业,我不建议轻易入行?

