某江app算法分析
2023-03-14 22:42:19 时间
一、抓包分析
1、数据包
GET http://m.api.zt.jsw.com.cn/v2/member?password=a123456&clientid=1&device_id=010067028741939&ip=1.1.1.1&system_name=android&sign=e96e177e2b9ed89680ac754916333527&siteid=10001&time=1630198142862&type=android&account=15836353612&modules=cloudlogin%3A1 HTTP/1.1 Content-Length: 0 Host: m.api.zt.jsw.com.cn Connection: Keep-Alive Accept-Encoding: gzip
2、分析参数,只有sign是密文

二、将app拖进jeb分析
1、搜索关键词"sign"
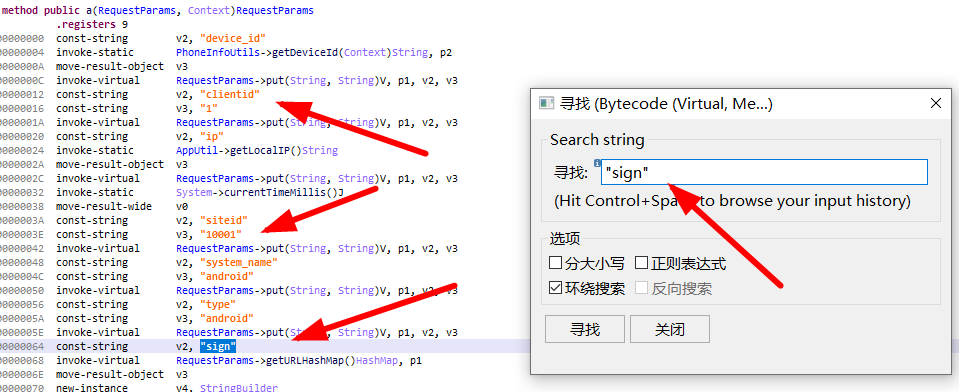
2、tab键转换成java代码,需要查看b.a方法
public RequestParams a(RequestParams params, Context context) { params.put("device_id", PhoneInfoUtils.getDeviceId(context)); params.put("clientid", "1"); params.put("ip", AppUtil.getLocalIP()); long timestamp = System.currentTimeMillis(); params.put("siteid", "10001"); params.put("system_name", "android"); params.put("type", "android"); params.put("sign", b.a(params.getURLHashMap(), timestamp + "")); params.put("time", timestamp + ""); return params; }
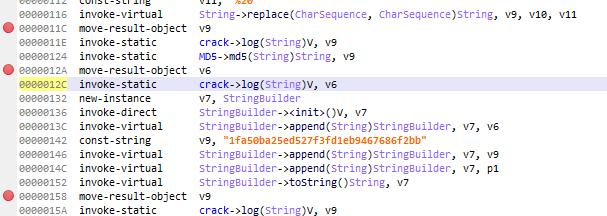
3、双击进入b.a方法,倒着看,v4是最终结果,v9_2是第一次md5,v6是第二次md5,v9_1是md5的参数
public static String a(HashMap arg14, String time) { LinkedHashMap sortParams = new LinkedHashMap(); Object[] key_arr = arg14.keySet().toArray(); Arrays.sort(key_arr); int v10; for(v10 = 0; v10 < key_arr.length; v10 = (((int)v9)) + 1) { Object key = key_arr[v10]; try { String v12 = key.toString(); String v9 = URLEncoder.encode(((String)arg14.get(key)).toString(), "UTF-8"); sortParams.put(v12, v9); } catch(UnsupportedEncodingException e) { e.printStackTrace(); } } StringBuilder result = new StringBuilder(); for(Object v1: sortParams.entrySet()) { Map.Entry entry = (Map.Entry)v1; if(result.length() > 0) { result.append("&"); } result.append(((String)entry.getKey())); result.append("="); result.append(((String)entry.getValue())); } String v9_1 = result.toString().replace("*", "%2A").replace("%7E", "~").replace("+", "%20"); crack.log(v9_1); String v6 = MD5.md5(v9_1); crack.log(v6); String v9_2 = v6 + "1fa50ba25ed527f3fd1eb9467686f2bb" + time; crack.log(v9_2); String v4 = MD5.md5(v9_2); crack.log(v4); return v4; }
4、在上面三处处下断
5、动态调试,触发断点
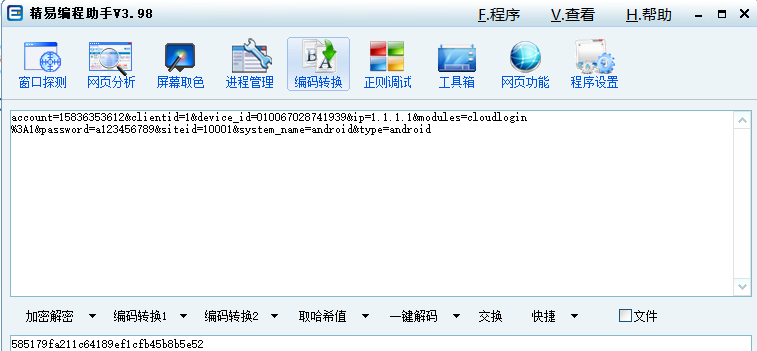
v9=account=15836353612&clientid=1&device_id=010067028741939&ip=1.1.1.1&modules=cloudlogin%3A1&password=a123456789&siteid=10001&system_name=android&type=android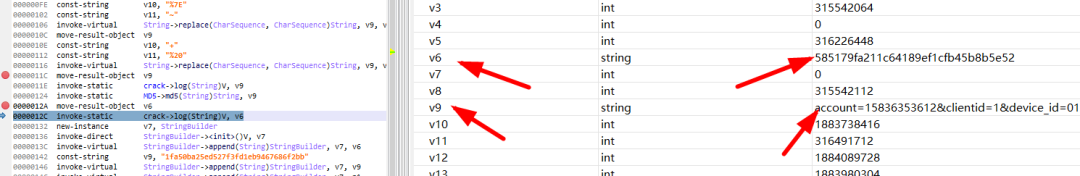
V6=585179fa211c64189ef1cfb45b8b5e526、v6是v9的md5值
7、第二个
v9=2db65aefd5f993ee290b7b709edc8f46+1fa50ba25ed527f3fd1eb9467686f2bb+1630223825602,再进行一次md5加密,记得去了+,这里只是让大家看清楚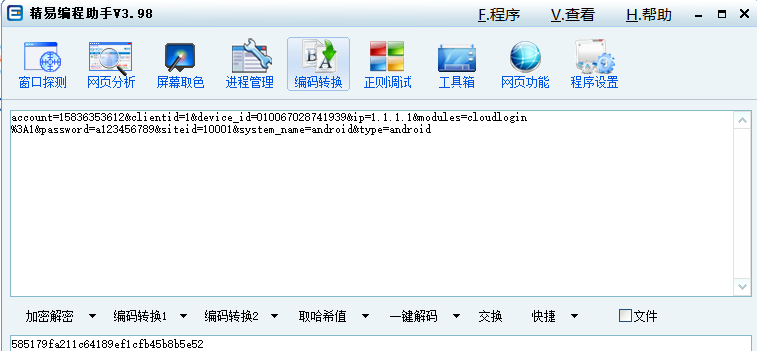
禁止非法,后果自负
相关文章
- 2015CIC大数据应用论坛,诸多看点提前报
- 数据挖掘在金融风险预警中的应用
- 说说对React中受控组件和非受控组件的理解?应用场景?
- 云时代的应用性能管理(APM)
- 译是如何把深度学习“塞进”手机的?
- 面试官:说说对React refs 的理解?应用场景?
- Dotnet Core 优雅的命令行实现
- 2021物联网开发的十种编程语言
- 字节二面:什么是 trie 树以及应用
- 制作QQ微信支付宝三合一收款码
- 前端自动化测试:Jest 测试框架应用
- Android编程开发之性能优化技巧
- Android面试被问到内存泄漏了杂整?
- Vite 的插件机制:插件应用和基本使用
- 号称能让开发者告别996,低代码火了,真神器还是伪风口
- 微信开放接口getUserInfo、login、getUserProfile的爱恨情仇?
- 2021 年加速开发的 8 个优秀跨平台框架
- 终于有人把SaaS讲明白了
- 【深入Node探究】(1)“Node特点与应用场景” 有四问
- 后国安局监控时代,用户最需要的体验是掌握隐私的自由

